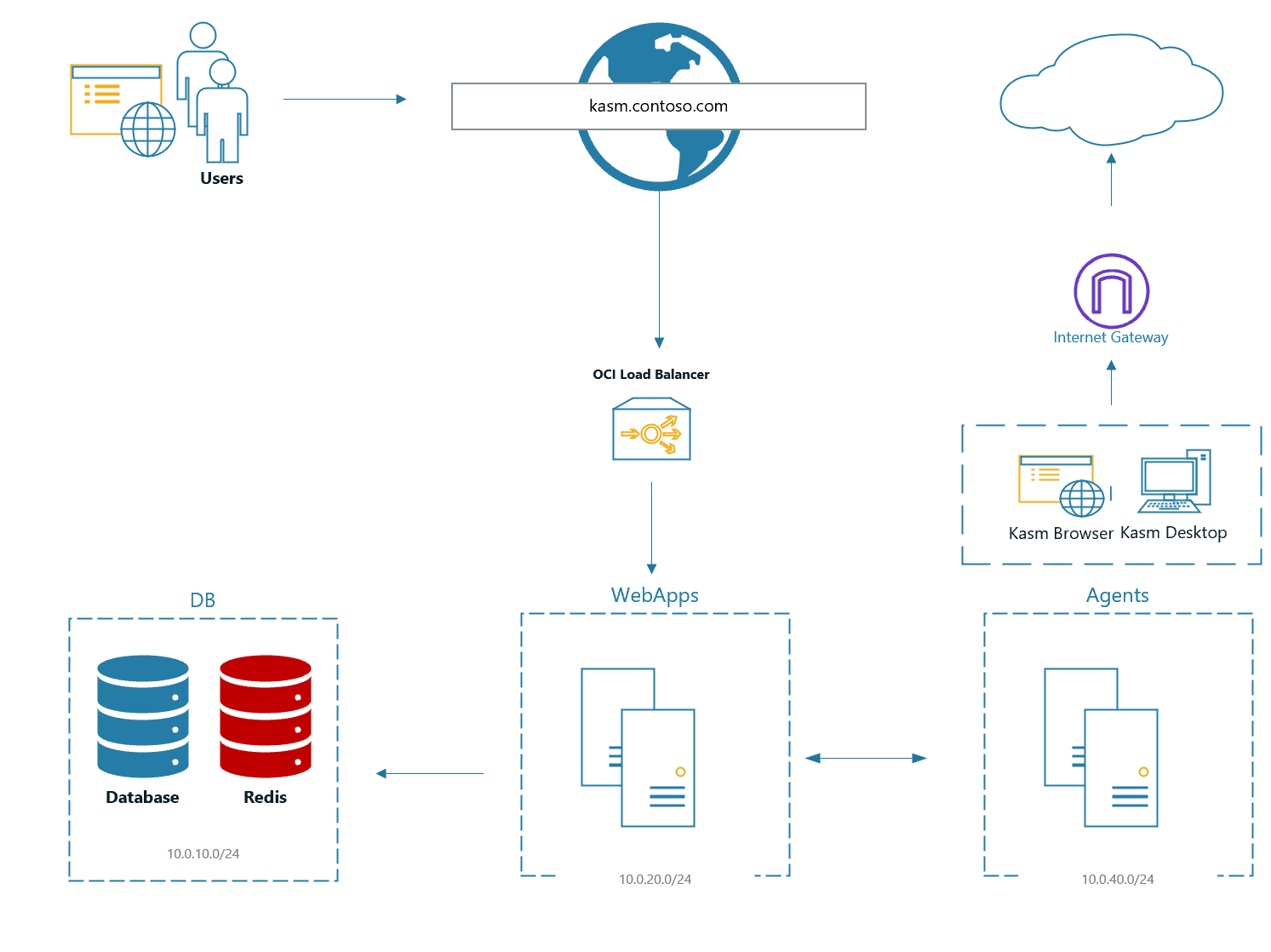
This project will deploy Kasm Workspaces in a multi-server deployment in OCI.
Consider creating a new Compartment for the Kasm Workspaces deployment.
In OCI create a public DNS zone that matches the desired domain name for the deployment. e.g kasm.contoso.com.
Create an administative user in the OCI console that will be used for the terraform deployment. Add the user to the Administrators Group. Generate an API Key for the user. The API Key Fingerprint will be used as a variable in the deployment configuration. Save the private key to the local directory replacing oci-private-key.pem.
To use Terraform to generate a Let's Encrypt certificate automatically, set the letsencrypt_cert_support_email to a valid email address and set the letsencrypt_server_type to either "staging" or "prod" and leave the kasm_ssl_crt_path and kasm_ssl_key_path variables empty.
NOTE:
- Staging generates certificates that a browser will not trust, but are formatted correctly and are designed for testing and validating the system configuraiton and deployment and has a limit of hundreds of certificates per domain per week.
- Prod generates trusted Let's Encrypt certificates but is limited to 5 certificates per week per domain.
Create an SSL certificate that matches the desired domain for the deployment. e.g (kasm.contoso.com). Place the pem encoded cert and key in this directory overwriting kasm_ssl.crt and kasm_ssl.key.
-
Initialize the project
terraform init -
Open
settings.tfvarsand update the variables. The variable definitions, descriptions, and validation requirements can be found invariables.tf, or in the table below. -
Verify the configuration
terraform plan -
Deploy
terraform apply -
Login to the Deployment as an Admin via the domain defined e.g
https://kasm.contoso.com. It may take several minutes for the deployment to fully come online.
| Name | Version |
|---|---|
| terraform | ~> 1.0 |
| acme | ~> 2.0 |
| oci | ~> 5.0 |
| tls | ~> 4.0 |
No providers.
| Name | Source | Version |
|---|---|---|
| kasm | ./module | n/a |
No resources.
| Name | Description | Type | Default | Required |
|---|---|---|---|---|
| admin_password | The administrative user password. No special characters | string |
n/a | yes |
| allow_ssh_cidrs | The CIDR notation to allow SSH access to the systems. | list(string) |
n/a | yes |
| allow_web_cidrs | The CIDR notation to allow HTTPS access to the systems. | list(string) |
n/a | yes |
| bastion_vm_settings | The number of CPUs, amount of memory in GB, and HDD size in GB to configure for the Kasm SSH Bastion instance | object({ |
n/a | yes |
| compartment_ocid | The Compartment OCID | string |
n/a | yes |
| database_password | The password for the database. No special characters | string |
n/a | yes |
| fingerprint | API Key Fingerprint | string |
n/a | yes |
| instance_image_ocid | The OCID for the instance image, such as ubuntu 22.04, to use. | string |
n/a | yes |
| instance_shape | The instance shape to use. Should be a Flex type. | string |
n/a | yes |
| kasm_agent_vm_settings | The number of CPUs, amount of memory in GB, and HDD size in GB to configure for the Kasm Agent instances | object({ |
n/a | yes |
| kasm_build_url | The URL for the Kasm Workspaces build | string |
n/a | yes |
| kasm_cpx_vm_settings | The number of CPUs, amount of memory in GB, and HDD size in GB to configure for the Kasm cpx RDP instances | object({ |
n/a | yes |
| kasm_database_vm_settings | The number of CPUs, amount of memory in GB, and HDD size in GB to configure for the Kasm Database instance | object({ |
n/a | yes |
| kasm_ssl_crt_path | The file path to the PEM encoded SSL Certificate | string |
"" |
no |
| kasm_ssl_key_path | The file path to the PEM encoded SSL Certificate Key | string |
"" |
no |
| kasm_webapp_vm_settings | The number of CPUs, amount of memory in GB, and HDD size in GB to configure for the Kasm WebApp instances | object({ |
n/a | yes |
| letsencrypt_cert_support_email | Email address to use for Let's Encrypt SSL certificates for OCI Deployment | string |
"" |
no |
| letsencrypt_server_type | SSL Server type to generate. Valid options are staging and prod, and prod certificates are limited to 5 certificates per week. | string |
"" |
no |
| manager_token | The manager token value for Agents to authenticate to webapps. No special characters | string |
n/a | yes |
| num_agents | The number of Agent Role Servers to create in the deployment | number |
n/a | yes |
| num_cpx_nodes | The number of cpx RDP Role Servers to create in the deployment | number |
n/a | yes |
| num_webapps | The number of WebApp role servers to create in the deployment | number |
n/a | yes |
| oci_domain_name | The public Zone used for the dns entries. This must already exist in the OCI account. (e.g kasm.contoso.com). The deployment will be accessed via this zone name via https | string |
n/a | yes |
| private_key_path | The path to the API Key PEM encoded Private Key | string |
n/a | yes |
| project_name | The name of the deployment (e.g dev, staging). A short single word | string |
n/a | yes |
| redis_password | The password for the Redis server. No special characters | string |
n/a | yes |
| region | The OCI Region eg: (us-ashburn-1) | string |
n/a | yes |
| service_registration_token | The service registration token value for cpx RDP servers to authenticate to webapps. No special characters | string |
n/a | yes |
| ssh_authorized_keys | The SSH Public Keys to be installed on the OCI compute instance | string |
n/a | yes |
| swap_size | The amount of swap (in MB) to configure inside the compute instances | number |
n/a | yes |
| tenancy_ocid | The Tenancy OCID. | string |
n/a | yes |
| user_ocid | The User OCID. | string |
n/a | yes |
| user_password | The standard (non administrator) user password. No special characters | string |
n/a | yes |
| vcn_subnet_cidr | VCN Subnet CIDR where you wish to deploy Kasm | string |
n/a | yes |
No outputs.