-
-
Notifications
You must be signed in to change notification settings - Fork 12.1k
Commit
This commit does not belong to any branch on this repository, and may belong to a fork outside of the repository.
✨ feat: Supports Cloudflare Zero Trust login (#3624)
* ✨ feat: Supports Cloudflare Zero Trust login * 📝 docs: add doc for Cloudflare Zero Trust * ♻️ refactor: cleanup * ♻️ refactor: rollback checks
- Loading branch information
1 parent
3f92adc
commit ac2bf68
Showing
7 changed files
with
224 additions
and
1 deletion.
There are no files selected for viewing
68 changes: 68 additions & 0 deletions
68
docs/self-hosting/advanced/auth/next-auth/cloudflare-zero-trust.mdx
This file contains bidirectional Unicode text that may be interpreted or compiled differently than what appears below. To review, open the file in an editor that reveals hidden Unicode characters.
Learn more about bidirectional Unicode characters
| Original file line number | Diff line number | Diff line change |
|---|---|---|
| @@ -0,0 +1,68 @@ | ||
| --- | ||
| title: Configuring Cloudflare Zero Trust Authentication Service for LobeChat | ||
| description: >- | ||
| Learn how to configure Cloudflare Zero Trust for Single Sign-On (SSO) for LobeChat, | ||
| including creating an application provider, setting environment variables, and | ||
| deployment instructions. | ||
| tags: | ||
| - Cloudflare Zero Trust | ||
| - Single Sign-On (SSO) | ||
| - LobeChat Authentication | ||
| - Environment Variables | ||
| - Deployment Instructions | ||
| --- | ||
|
|
||
| # Configuring Cloudflare Zero Trust Authentication Service | ||
|
|
||
| ## Cloudflare Zero Trust Configuration Flow | ||
|
|
||
| <Steps> | ||
| ### Creating an Application in Cloudflare Zero Trust | ||
|
|
||
| We assume you are already familiar with using the Cloudflare Zero Trust platform and that your LobeChat instance is deployed at `https://chat.example.com`. | ||
|
|
||
| First, we need to visit `https://one.dash.cloudflare.com/` and navigate to `Access - Applications`. | ||
|
|
||
| 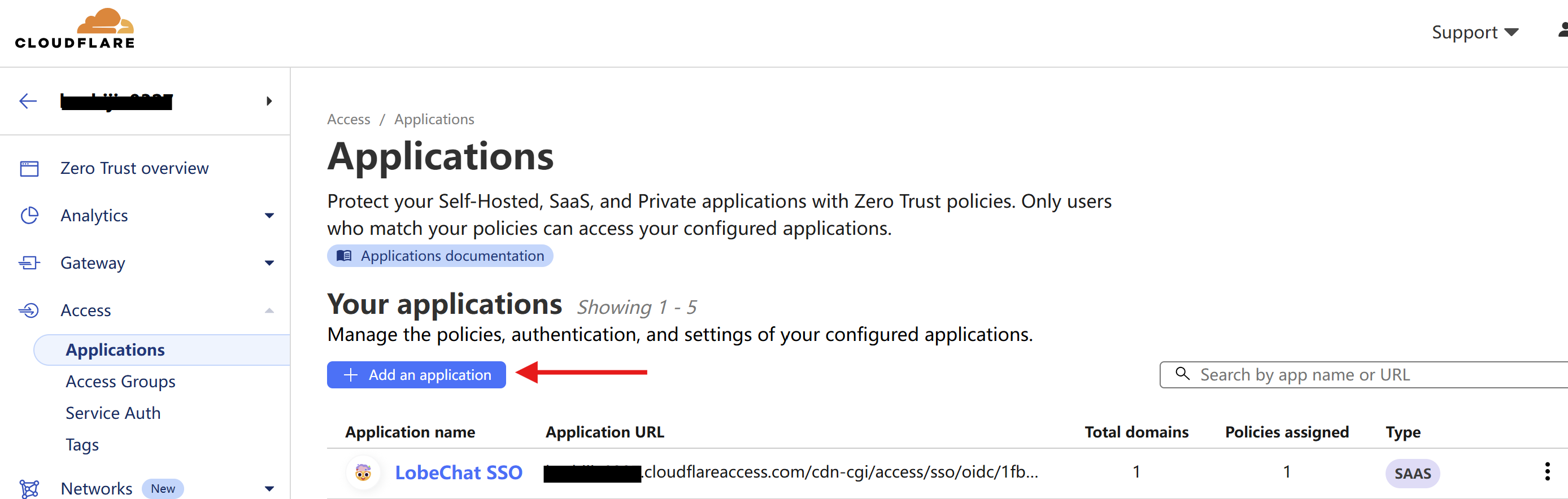 | ||
|
|
||
| Now, on the current page, click `Add an application` and select `SaaS`. | ||
|
|
||
| 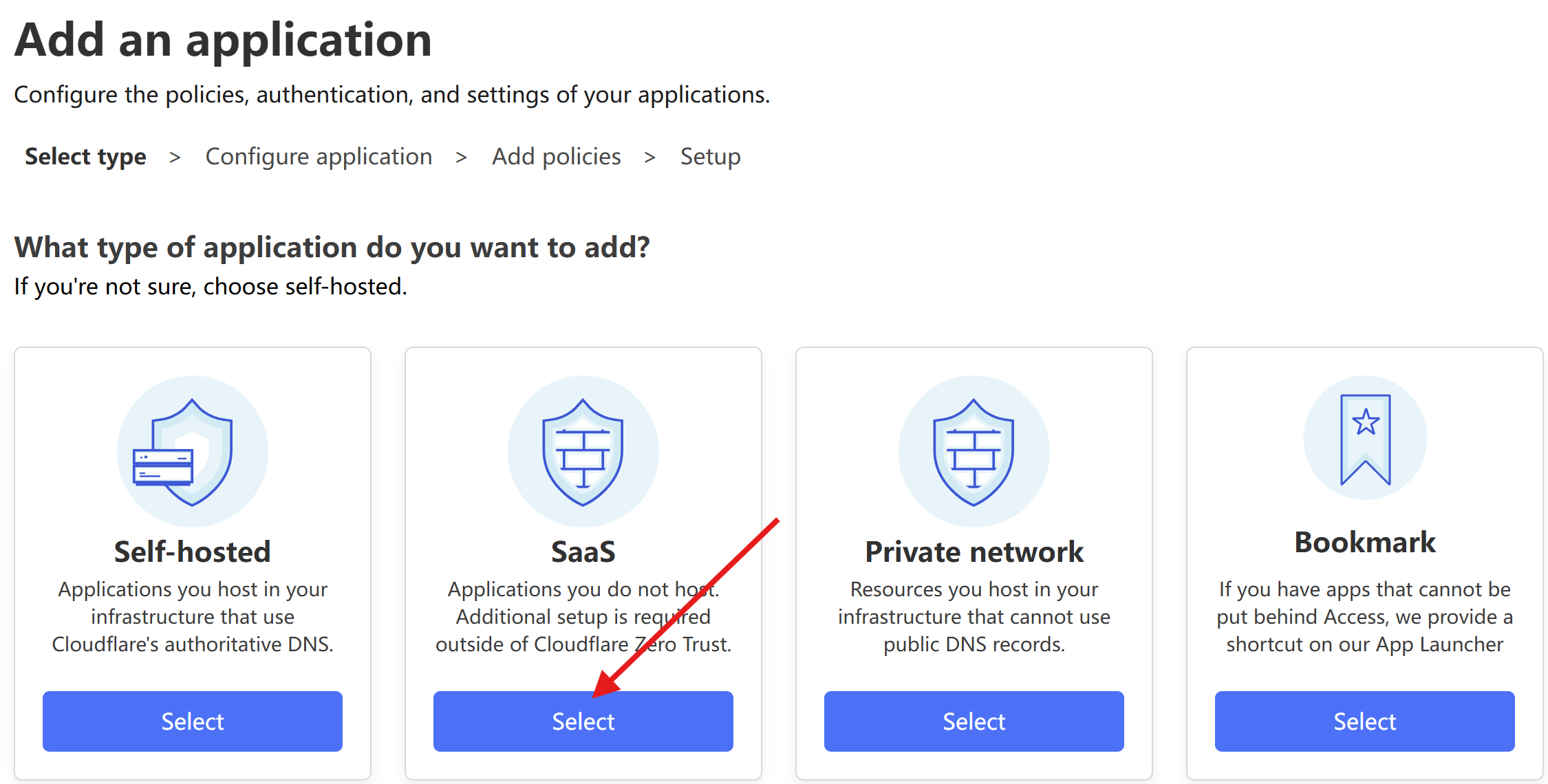 | ||
|
|
||
| In the `Application` text box, enter the application name, such as `LobeChat SSO`. Then click `Select OIDC`, followed by clicking `Add application`. | ||
|
|
||
| 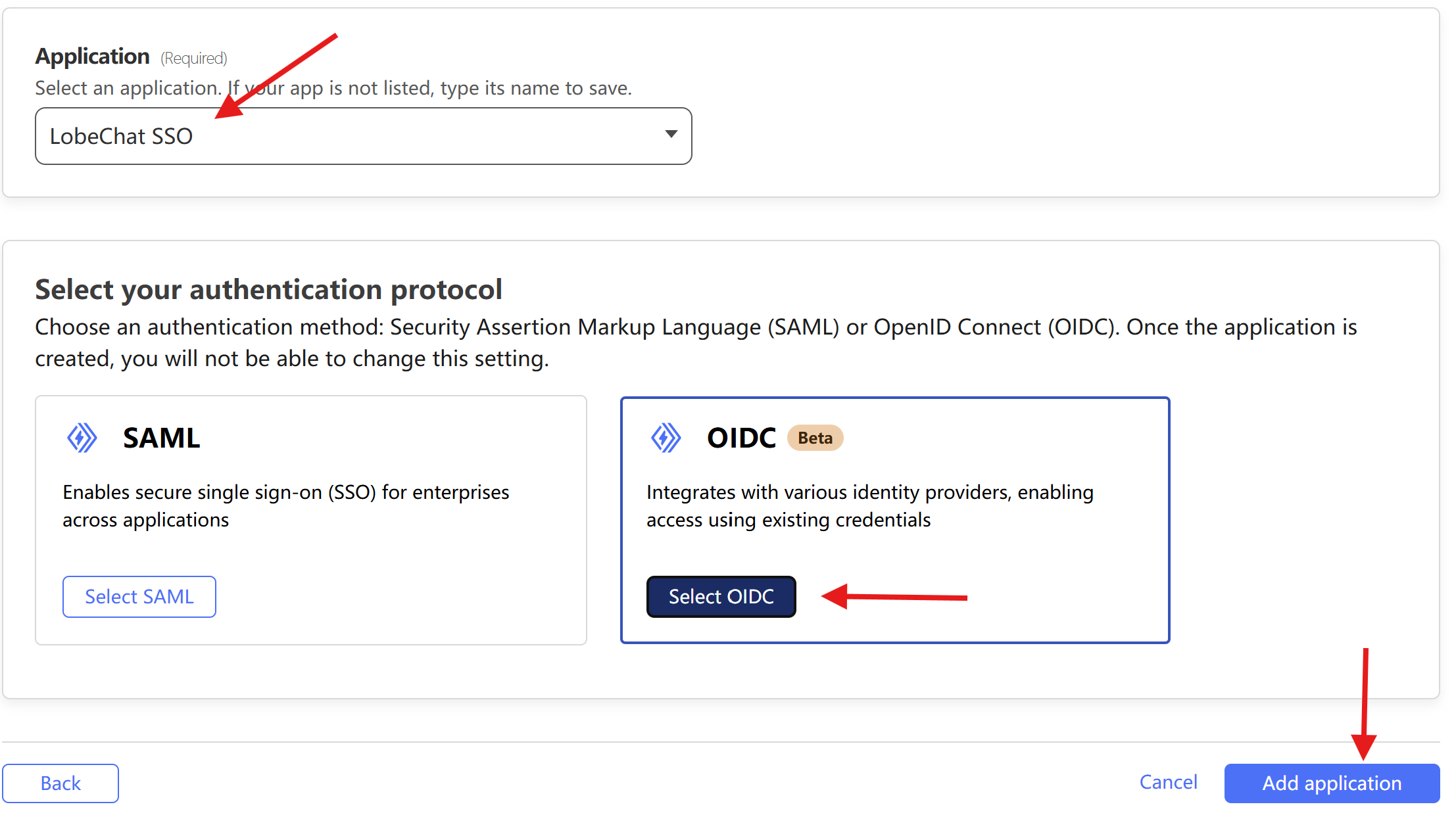 | ||
|
|
||
| At this point, you have successfully created a SaaS application named `LobeChat SSO` in Cloudflare Zero Trust. | ||
|
|
||
| Next, we need to enter `https://chat.example.com/api/auth/callback/cloudflare-zero-trust` in the `Redirect URLs` field (note that `chat.example.com` should be replaced with your instance's address). | ||
|
|
||
| 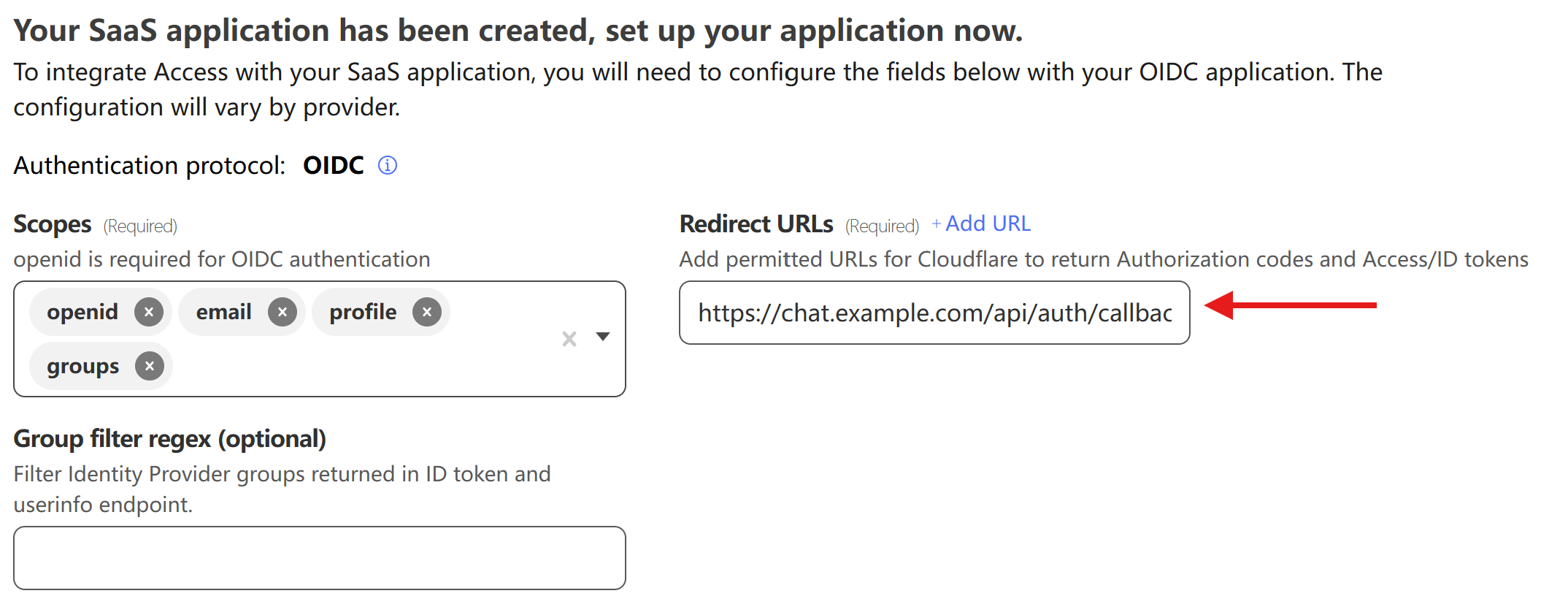 | ||
|
|
||
| Finally, scroll down the page and record the following three values: `Client secret`, `Client ID`, and `Issuer`. You will need these for setting the environment variables when deploying LobeChat. | ||
|
|
||
| 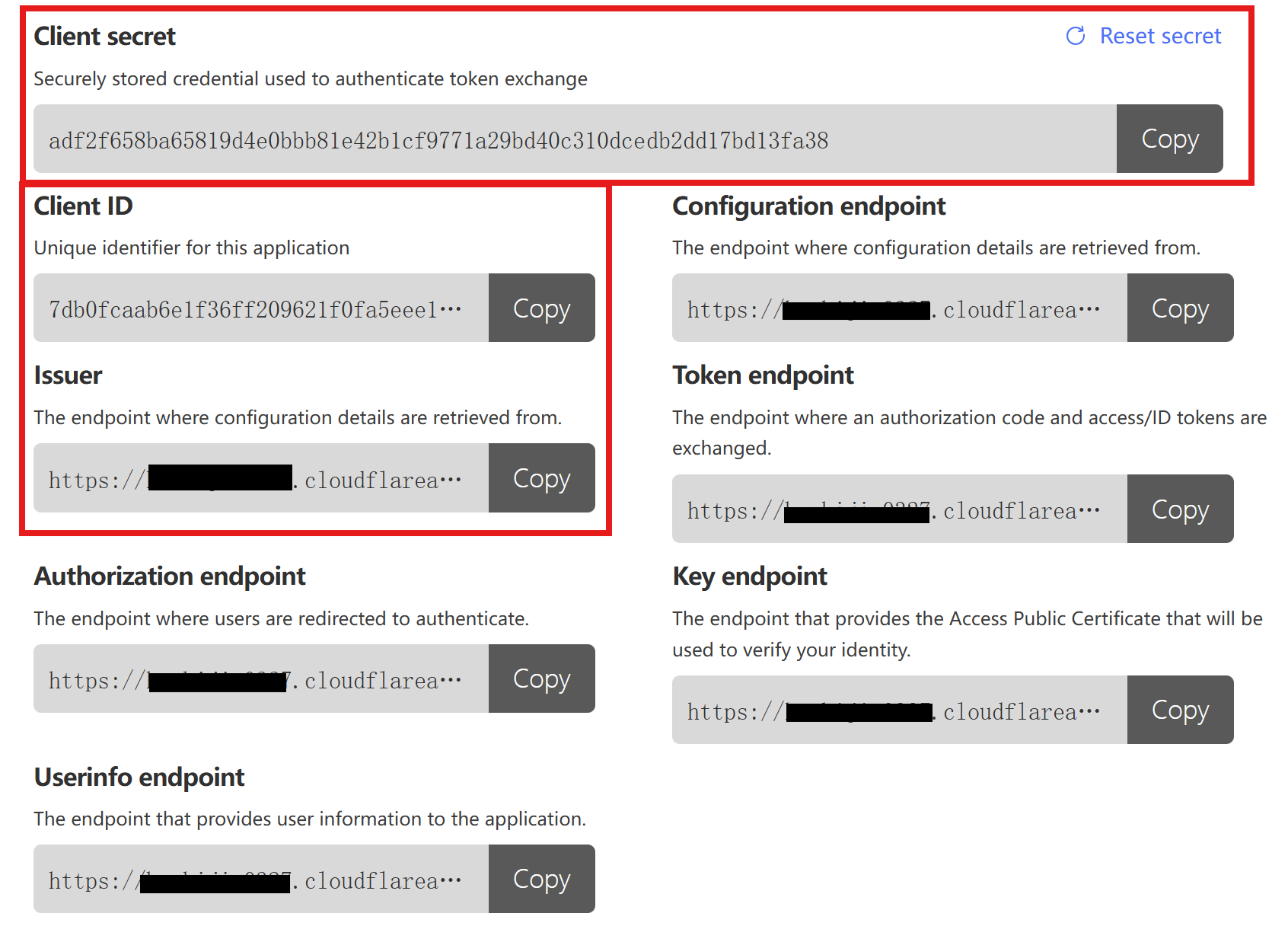 | ||
|
|
||
| ### Configure Environment Variables | ||
|
|
||
| When deploying LobeChat, you need to configure the following environment variables: | ||
|
|
||
| | Environment Variable | Type | Description | | ||
| | --- | --- | --- | | ||
| | `NEXT_AUTH_SECRET` | Required | The secret used to encrypt Auth.js session tokens. You can generate a secret using the following command: `openssl rand -base64 32` | | ||
| | `NEXT_AUTH_SSO_PROVIDERS` | Required | Select the SSO provider for LoboChat. Use `cloudflare-zero-trust` for Cloudflare Zero Trust. | | ||
| | `CLOUDFLARE_ZERO_TRUST_CLIENT_ID` | Required | The Client ID from the Cloudflare Zero Trust application provider details page | | ||
| | `CLOUDFLARE_ZERO_TRUST_CLIENT_SECRET` | Required | The Client Secret from the Cloudflare Zero Trust application provider details page | | ||
| | `CLOUDFLARE_ZERO_TRUST_ISSUER` | Required | The OpenID Configuration Issuer from the Cloudflare Zero Trust application provider details page | | ||
| | `NEXTAUTH_URL` | Optional | This URL is used to specify the callback address for Auth.js when performing OAuth authentication. It only needs to be set when the default generated redirect address is incorrect. `https://example.com/api/auth` | | ||
|
|
||
| <Callout type={'tip'}> | ||
| Go to [📘 Environment Variables](/docs/self-hosting/environment-variable#Cloudflare%20Zero%20Trust) for details about the variables. | ||
|
|
||
| </Callout> | ||
| </Steps> | ||
|
|
||
| <Callout type={'info'}> | ||
| After a successful deployment, users will be able to use LobeChat by authenticating with the users | ||
| configured in Cloudflare Zero Trust. | ||
| </Callout> |
63 changes: 63 additions & 0 deletions
63
docs/self-hosting/advanced/auth/next-auth/cloudflare-zero-trust.zh-CN.mdx
This file contains bidirectional Unicode text that may be interpreted or compiled differently than what appears below. To review, open the file in an editor that reveals hidden Unicode characters.
Learn more about bidirectional Unicode characters
| Original file line number | Diff line number | Diff line change |
|---|---|---|
| @@ -0,0 +1,63 @@ | ||
| --- | ||
| title: 在 LobeChat 中配置 Cloudflare Zero Trust 身份验证服务 | ||
| description: 学习如何在 LobeChat 中配置 Cloudflare Zero Trust 身份验证服务,包括创建提供程序、配置环境变量和部署 LobeChat。详细步骤和必要环境变量设置。 | ||
| tags: | ||
| - Cloudflare Zero Trust | ||
| - 身份验证 | ||
| - 单点登录 | ||
| - 环境变量 | ||
| - LobeChat | ||
| --- | ||
|
|
||
| # 配置 Cloudflare Zero Trust 身份验证服务 | ||
|
|
||
| ## Cloudflare Zero Trust 配置流程 | ||
|
|
||
| <Steps> | ||
| ### 在 Cloudflare Zero Trust 中创建应用 | ||
|
|
||
| 我们现在默认您已经了解了如何使用 Cloudflare Zero Trust 平台且假设您的 LobeChat 实例部署在 `https://chat.example.com` 中。 | ||
|
|
||
| 首先我们需要访问 `https://one.dash.cloudflare.com/` 并前往 `Access - Applications` 中。 | ||
|
|
||
|  | ||
|
|
||
| 现在,在所在页面点击 `Add an application` 并选择 `SaaS`。 | ||
|
|
||
|  | ||
|
|
||
| 在 `Application` 文本框内填入应用名称,如:`LobeChat SSO`,然后点击 `Select OIDC` 后点击 `Add applicaiton` | ||
|
|
||
|  | ||
|
|
||
| 至此您已成功在 Clouflare Zero Trust 中创建了一个名为 `LobeChat SSO` 的 SaaS 应用。 | ||
|
|
||
| 接下来我们需要在 `Redirect URLs` 中填入 `https://chat.example.com/api/auth/callback/cloudflare-zero-trust`(注意此处的 `chat.example.com` 需要替换为您的实例地址) | ||
|  | ||
|
|
||
| 最后我们将页面往下滚动,您将需要记录以下三个值 `Client secret`, `Client ID` 及 `Issuer` 以备后续部署 LobeChat 环境变量使用。 | ||
|
|
||
|  | ||
|
|
||
| ### 配置环境变量 | ||
|
|
||
| 在部署 LobeChat 时,你需要配置以下环境变量: | ||
|
|
||
| | 环境变量 | 类型 | 描述 | | ||
| | --- | --- | --- | | ||
| | `NEXT_AUTH_SECRET` | 必选 | 用于加密 Auth.js 会话令牌的密钥。您可以使用以下命令生成秘钥: `openssl rand -base64 32` | | ||
| | `NEXT_AUTH_SSO_PROVIDERS` | 必选 | 选择 LoboChat 的单点登录提供商。使用 Cloudflare Zero Trust 请填写 `cloudflare-zero-trust`。 | | ||
| | `CLOUDFLARE_ZERO_TRUST_CLIENT_ID` | 必选 | 在 Cloudflare Zero Trust 生成的 `Client ID`,示例值是 `lobe-chat` | | ||
| | `CLOUDFLARE_ZERO_TRUST_CLIENT_SECRET` | 必选 | 在 Cloudflare Zero Trust 生成的 `Client secret`,示例值是 `insecure_secret` | | ||
| | `CLOUDFLARE_ZERO_TRUST_ISSUER` | 必选 | 在 Cloudflare Zero Trust 生成的 `Issuer`,例如 `https://example.cloudflareaccess.com/cdn-cgi/access/sso/oidc/7db0f` | | ||
| | `NEXTAUTH_URL` | 可选 | 该 URL 用于指定 Auth.js 在执行 OAuth 验证时的回调地址,当默认生成的重定向地址发生不正确时才需要设置。`https://chat.example.com/api/auth` | | ||
|
|
||
| <Callout type={'tip'}> | ||
| 前往 [📘 环境变量](/docs/self-hosting/environment-variable#Cloudflare%20Zero%20Trust) 可查阅相关变量详情。 | ||
|
|
||
| </Callout> | ||
| </Steps> | ||
|
|
||
| <Callout type={'info'}> | ||
| 部署成功后,用户将可以使用 Cloudflare Zero Trust 中配置的用户通过身份认证并使用 LobeChat。 | ||
| </Callout> |
This file contains bidirectional Unicode text that may be interpreted or compiled differently than what appears below. To review, open the file in an editor that reveals hidden Unicode characters.
Learn more about bidirectional Unicode characters
This file contains bidirectional Unicode text that may be interpreted or compiled differently than what appears below. To review, open the file in an editor that reveals hidden Unicode characters.
Learn more about bidirectional Unicode characters
This file contains bidirectional Unicode text that may be interpreted or compiled differently than what appears below. To review, open the file in an editor that reveals hidden Unicode characters.
Learn more about bidirectional Unicode characters
This file contains bidirectional Unicode text that may be interpreted or compiled differently than what appears below. To review, open the file in an editor that reveals hidden Unicode characters.
Learn more about bidirectional Unicode characters
| Original file line number | Diff line number | Diff line change |
|---|---|---|
| @@ -0,0 +1,35 @@ | ||
| import type { OIDCConfig } from '@auth/core/providers'; | ||
|
|
||
| import { authEnv } from '@/config/auth'; | ||
|
|
||
| import { CommonProviderConfig } from './sso.config'; | ||
|
|
||
| export type CloudflareZeroTrustProfile = { | ||
| email: string; | ||
| name: string; | ||
| sub: string; | ||
| }; | ||
|
|
||
| const provider = { | ||
| id: 'cloudflare-zero-trust', | ||
| provider: { | ||
| ...CommonProviderConfig, | ||
| authorization: { params: { scope: 'openid email profile' } }, | ||
| checks: ['state', 'pkce'], | ||
| clientId: authEnv.CLOUDFLARE_ZERO_TRUST_CLIENT_ID, | ||
| clientSecret: authEnv.CLOUDFLARE_ZERO_TRUST_CLIENT_SECRET, | ||
| id: 'cloudflare-zero-trust', | ||
| issuer: authEnv.CLOUDFLARE_ZERO_TRUST_ISSUER, | ||
| name: 'Cloudflare Zero Trust', | ||
| profile(profile) { | ||
| return { | ||
| email: profile.email, | ||
| name: profile.name, | ||
| providerAccountId: profile.sub, | ||
| }; | ||
| }, | ||
| type: 'oidc', | ||
| } satisfies OIDCConfig<CloudflareZeroTrustProfile>, | ||
| }; | ||
|
|
||
| export default provider; |
This file contains bidirectional Unicode text that may be interpreted or compiled differently than what appears below. To review, open the file in an editor that reveals hidden Unicode characters.
Learn more about bidirectional Unicode characters