-
Notifications
You must be signed in to change notification settings - Fork 33
OpenID Connect
psunix edited this page Apr 6, 2021
·
9 revisions
With Version > 3.6 Cryptopus supports Single-Sign-On (SSO) with OpenID Connect / Keycloak
Cryptopus expects an ID-Token containing a claim named cryptops_pk_secret_base with a 32 characters longs alphanumeric secret for each user.
Check Keycloak Development Setup for a working example using Keycloak.
This Setup with Keycloak is based on RandomString OIDC Mapper.
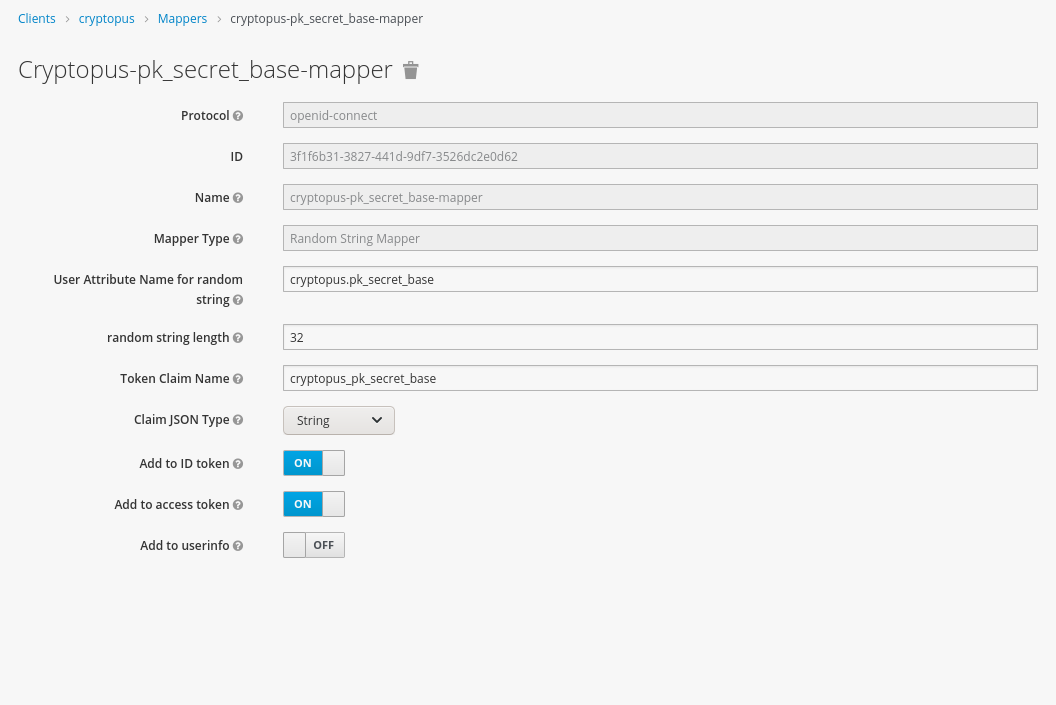
- Token Claim Name: cryptopus_pk_secret_base
- User Attribute Name for random string: cryptopus.pk_secret_base
override existing config/auth.yml:
provider: openid-connect
oidc:
client_id: cryptopus
host: my-keycloak
host_port: 443
host_scheme: https
secret: 'my-oidc-secret'
authorization_endpoint: '/auth/realms/my-realm/protocol/openid-connect/auth'
token_endpoint: '/auth/realms/my-realm/protocol/openid-connect/token'
user_subject: preferred_username
certs_url: https://my-keycloak/auth/realms/my-realm/protocol/openid-connect/certs
additional_scopes:
- email