-
Notifications
You must be signed in to change notification settings - Fork 816
New issue
Have a question about this project? Sign up for a free GitHub account to open an issue and contact its maintainers and the community.
By clicking “Sign up for GitHub”, you agree to our terms of service and privacy statement. We’ll occasionally send you account related emails.
Already on GitHub? Sign in to your account
There is a "Unsafe Unzip" vulnerability that can get webshell #13
Comments
|
So it's a shell upload in background, requires administrator authorization? |
|
@unh3x |
sanluan
added a commit
that referenced
this issue
Jun 28, 2018
Sign up for free
to join this conversation on GitHub.
Already have an account?
Sign in to comment

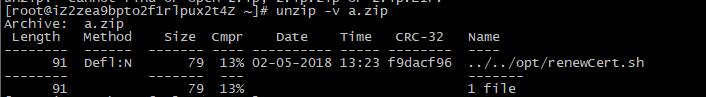



ver: V4.0.20180210
using a specially crafted zip archive, that holds path traversal filenames.when you used unzip method you will get a shell
a zip looks like this:

the path you will get from there:

(so,your website true path is 'C:\tomcat\apache-tomcat-7.0.81\apache-tomcat-7.0.81\webapps\publiccms')
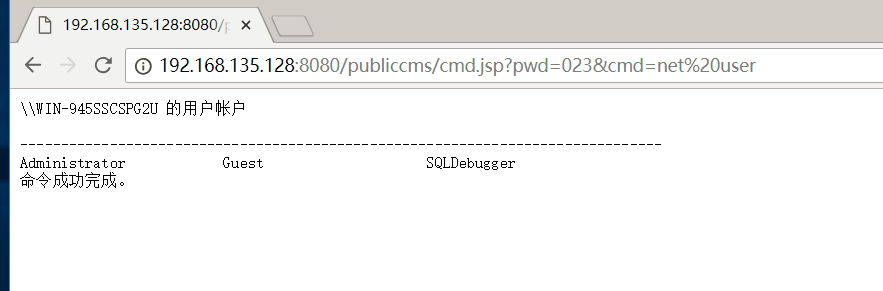
upload and unzip
'cmd.jsp' will write into your server
Execute the command
shell.zip
The text was updated successfully, but these errors were encountered: