-
-
Notifications
You must be signed in to change notification settings - Fork 13
New issue
Have a question about this project? Sign up for a free GitHub account to open an issue and contact its maintainers and the community.
By clicking “Sign up for GitHub”, you agree to our terms of service and privacy statement. We’ll occasionally send you account related emails.
Already on GitHub? Sign in to your account
feat(#89): add support for pulling the Locust image from private registries #98
feat(#89): add support for pulling the Locust image from private registries #98
Conversation
2ed7a23 to
5ca9d73
Compare
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
Thank you for your kind contribution. It is something that is truly appreciated. I would also like to add additional recognition of writing code that feels native to the implementation already in place.
All and all, amazing work. I have left few comments that I believe are missing to make this PR complete. I would also kindly ask you to include some screenshots / snippets of the generated jobs / pods running with this option. This is so i don't have to setup a private registry myself somewhere and try to test this.
As always nothing is set in stone and everything can be discussed if you have a different opinion.
src/main/java/com/locust/operator/controller/utils/LoadGenHelpers.java
Outdated
Show resolved
Hide resolved
src/main/java/com/locust/operator/controller/utils/LoadGenHelpers.java
Outdated
Show resolved
Hide resolved
.../java/com/locust/operator/controller/utils/resource/manage/ResourceCreationManagerTests.java
Outdated
Show resolved
Hide resolved
.../java/com/locust/operator/controller/utils/resource/manage/ResourceCreationManagerTests.java
Outdated
Show resolved
Hide resolved
src/test/java/com/locust/operator/controller/utils/TestFixtures.java
Outdated
Show resolved
Hide resolved
|
Hello @jachinte, |
Co-authored-by: Abdelrhman Hamouda <[email protected]>
Co-authored-by: Abdelrhman Hamouda <[email protected]>
Co-authored-by: Abdelrhman Hamouda <[email protected]>
…hmanHamouda#98) Co-authored-by: Abdelrhman Hamouda <[email protected]>
…manHamouda#98) Co-authored-by: Abdelrhman Hamouda <[email protected]>
…hmanHamouda#98) Co-authored-by: Abdelrhman Hamouda <[email protected]>
Co-authored-by: Abdelrhman Hamouda <[email protected]>
…hmanHamouda#98) Co-authored-by: Abdelrhman Hamouda <[email protected]>
…manHamouda#98) Co-authored-by: Abdelrhman Hamouda <[email protected]>
…hmanHamouda#98) Co-authored-by: Abdelrhman Hamouda <[email protected]>
Co-authored-by: Abdelrhman Hamouda <[email protected]>
…from private registries (AbdelrhmanHamouda#98)
b04034b to
7b257c4
Compare
…from private registries (AbdelrhmanHamouda#98)
7b257c4 to
d3c554c
Compare
…from private registries (AbdelrhmanHamouda#98)
d3c554c to
59ed7b7
Compare
|
Hi @AbdelrhmanHamouda, I've applied the changes you suggested. I also added the the missing option Here are some screenshots using a private image from the Github Container Registry, on a local k3s cluster: Create a local cluster using k3d
Create the target namespace and a configmap based on the test module
Install the operator in the target namespaceNote that I packaged the operator locally and published a custom image to Docker Hub
Create a secret in the target namespace for using the Github Container Registry
The custom resource
Deploy the custom resource and monitor created jobs, pods and locust tests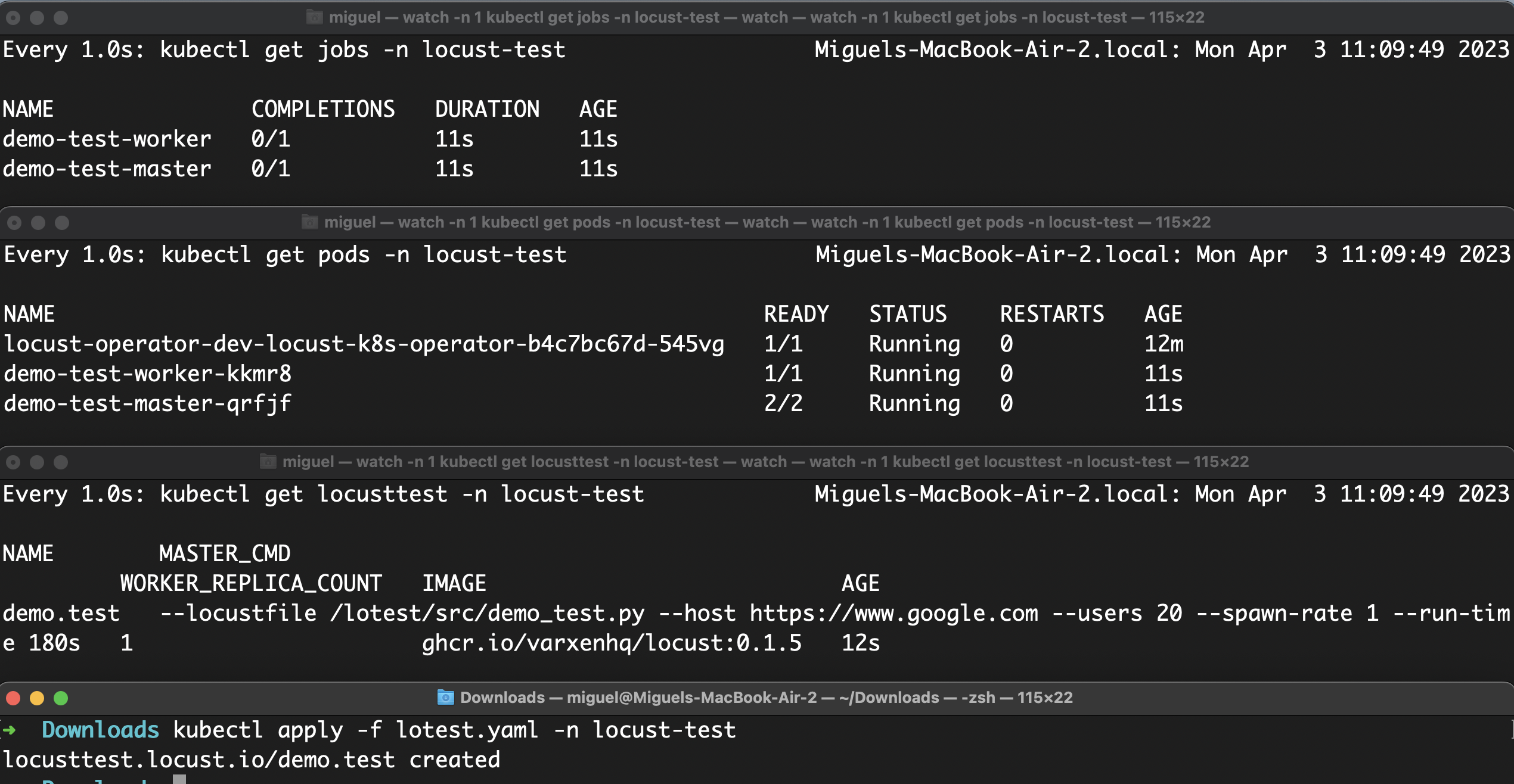
Inspect the latest events to confirm everything worked as expected
|
|
thank you for the nice contribution. The failing test seems to be coming from a change in the github action that is not related to this PR. I will have to work on it independently |
|
@jachinte As expected that merging the other PRs caused a conflict on this one. I would resolve it myself but I see that you didn't allow changes by the reviewer. To be this PR is ready to merge, simply solve the conflict and I will merge directly. |
Codecov Report
@@ Coverage Diff @@
## master #98 +/- ##
=========================================
Coverage 94.70% 94.70%
Complexity 79 79
=========================================
Files 12 12
Lines 378 378
Branches 11 11
=========================================
Hits 358 358
Misses 16 16
Partials 4 4
Help us with your feedback. Take ten seconds to tell us how you rate us. Have a feature suggestion? Share it here. |
|
@AbdelrhmanHamouda I've resolved the merge conflicts. |
This pull request implements the feature proposed in #89
I've added some documentation in the getting started page.
Please let me know your thoughts on this PR.
Note that I could've used Helm's convention to specify images (i.e., an
imageobject with propertiesrepository,tagandpullPolicy, plus an additional propertyimagePullSecrets) but decided against this because the operator already uses the keyimage. Doing so would've introduced a breaking change.