-
Notifications
You must be signed in to change notification settings - Fork 8.3k
New issue
Have a question about this project? Sign up for a free GitHub account to open an issue and contact its maintainers and the community.
By clicking “Sign up for GitHub”, you agree to our terms of service and privacy statement. We’ll occasionally send you account related emails.
Already on GitHub? Sign in to your account
[Cloud Security] CNVM: Error Persists in Kibana Search with Asterisk (*) and No Double Quotes #157954
Comments
|
Pinging @elastic/kibana-cloud-security-posture (Team:Cloud Security) |
|
After syncing with @nick-alayil - this is not a showstopper for 8.8. |
|
DOD: give a way to recover from that error |
|
created a draft PR fixing points 1 and 2 from my comment , will look into 3 |
|
added the support for point 3 ( |
|
@nick-alayil can you take a look at this comment #157954 (comment) and check if the proposed fixes make sense? I already implemented all three, so no need for additional tickets if you agree with the fixes |
…dling when it is disabled (#162555) ## Summary The PR: - fixes #157954 - allows a user to recover from #157954 by rendering the search bar even when an error occurs (in line with how Misconfiguration behaves) - enables the support of `query:allowLeadingWildcard` setting of Kibana - fixes unhandled exception on Resource Vulnerabilities page - fixes the loading state on the search bar in Vulnerabilities which wasn't working before 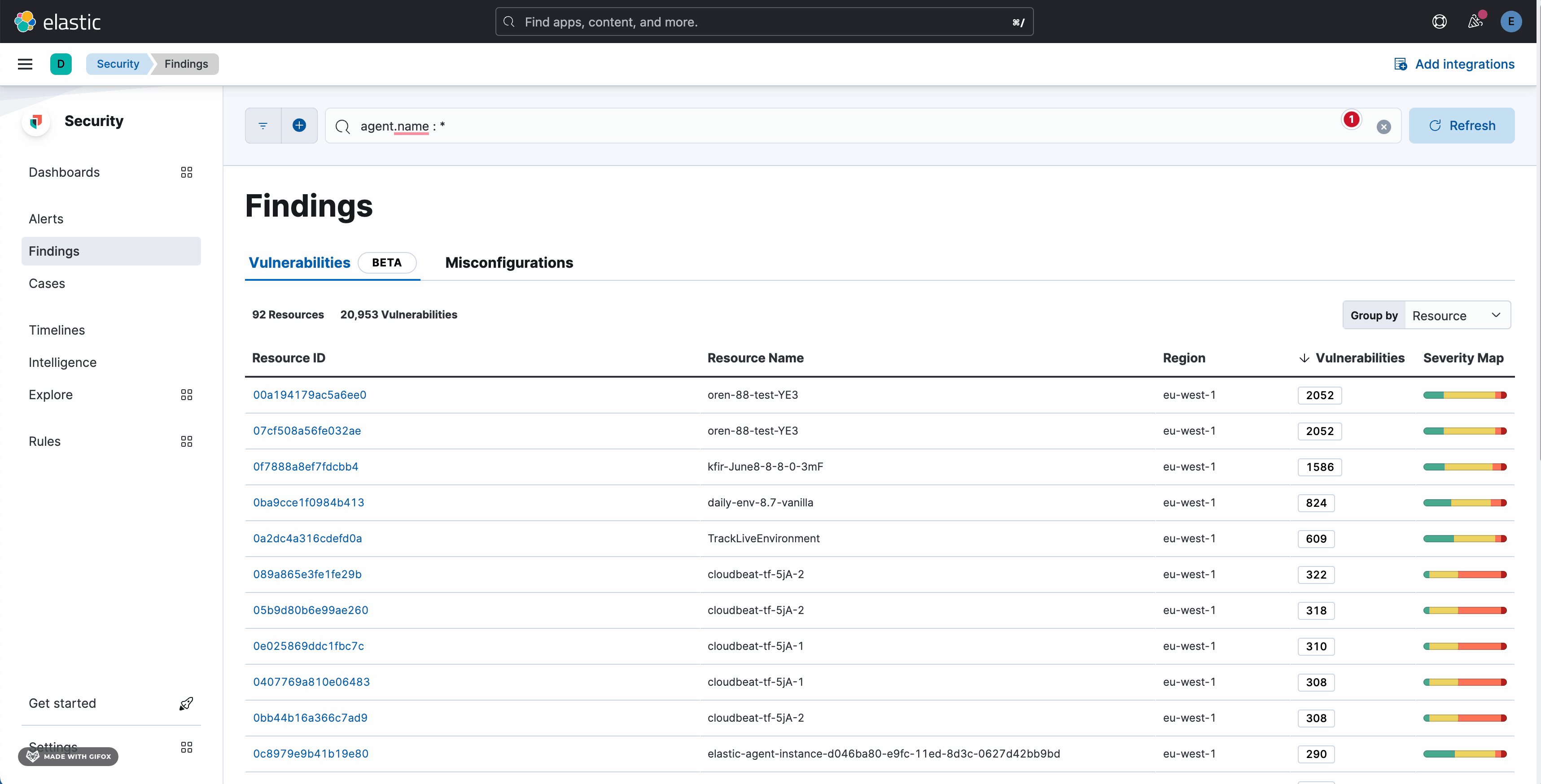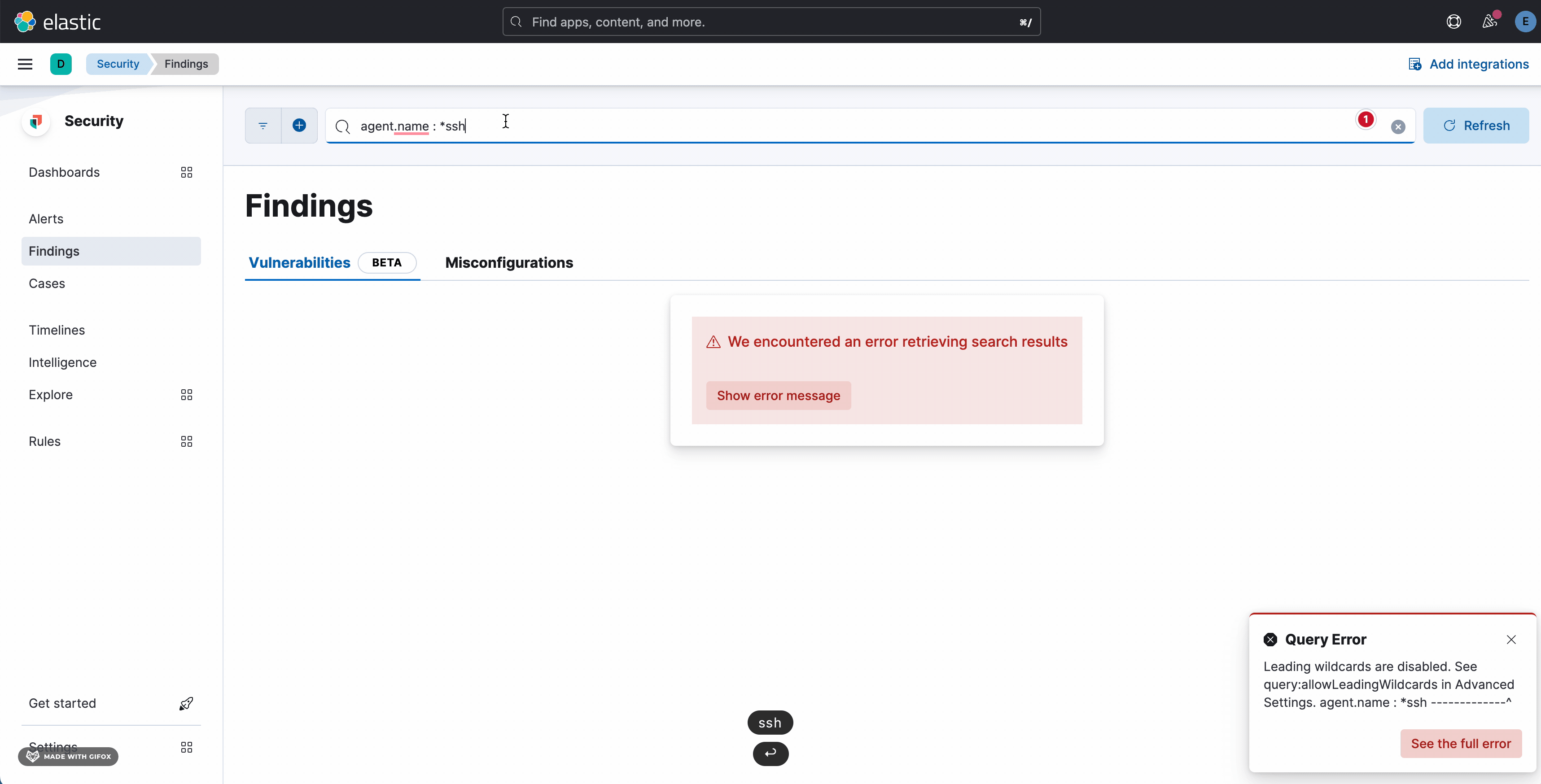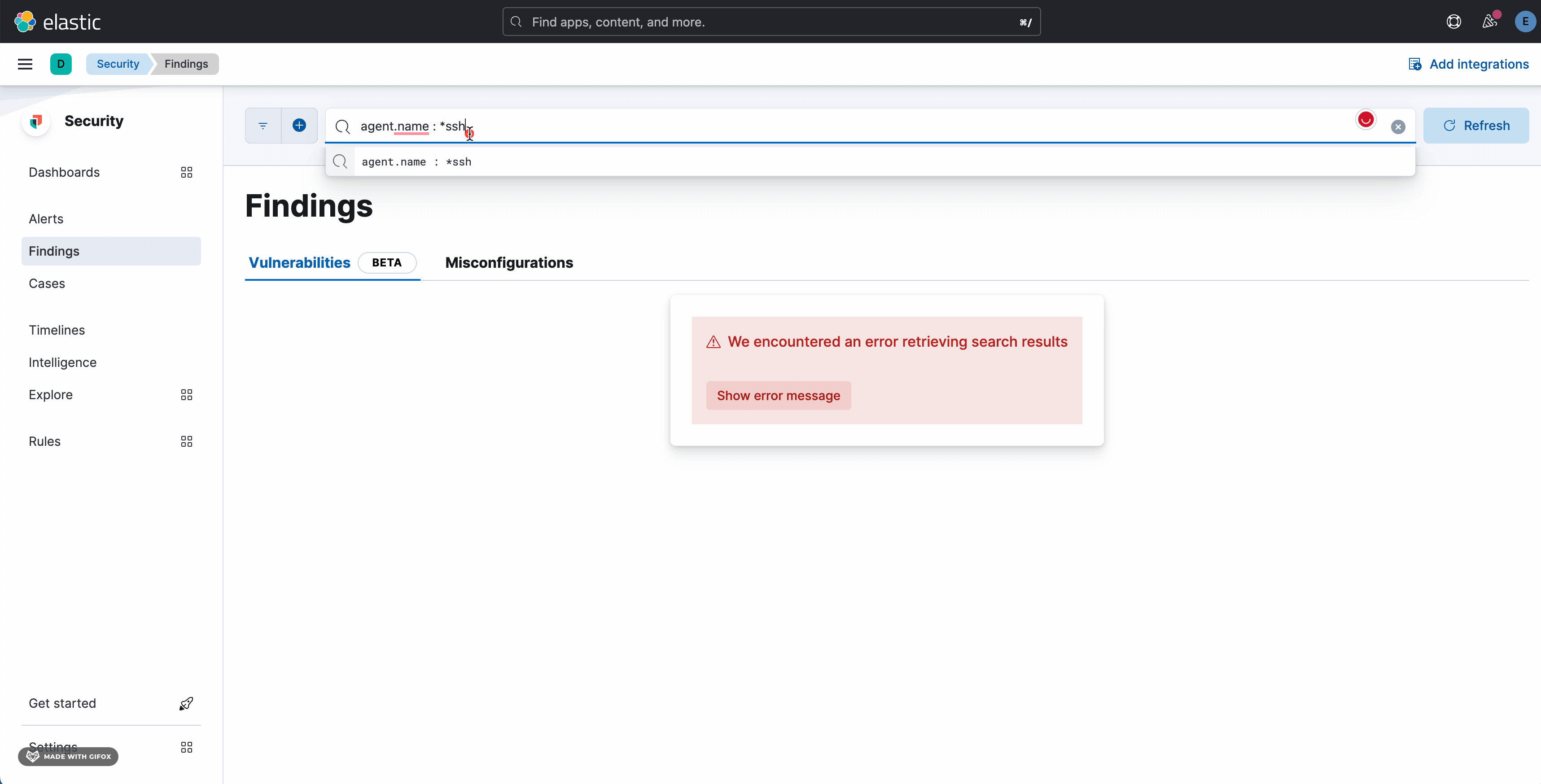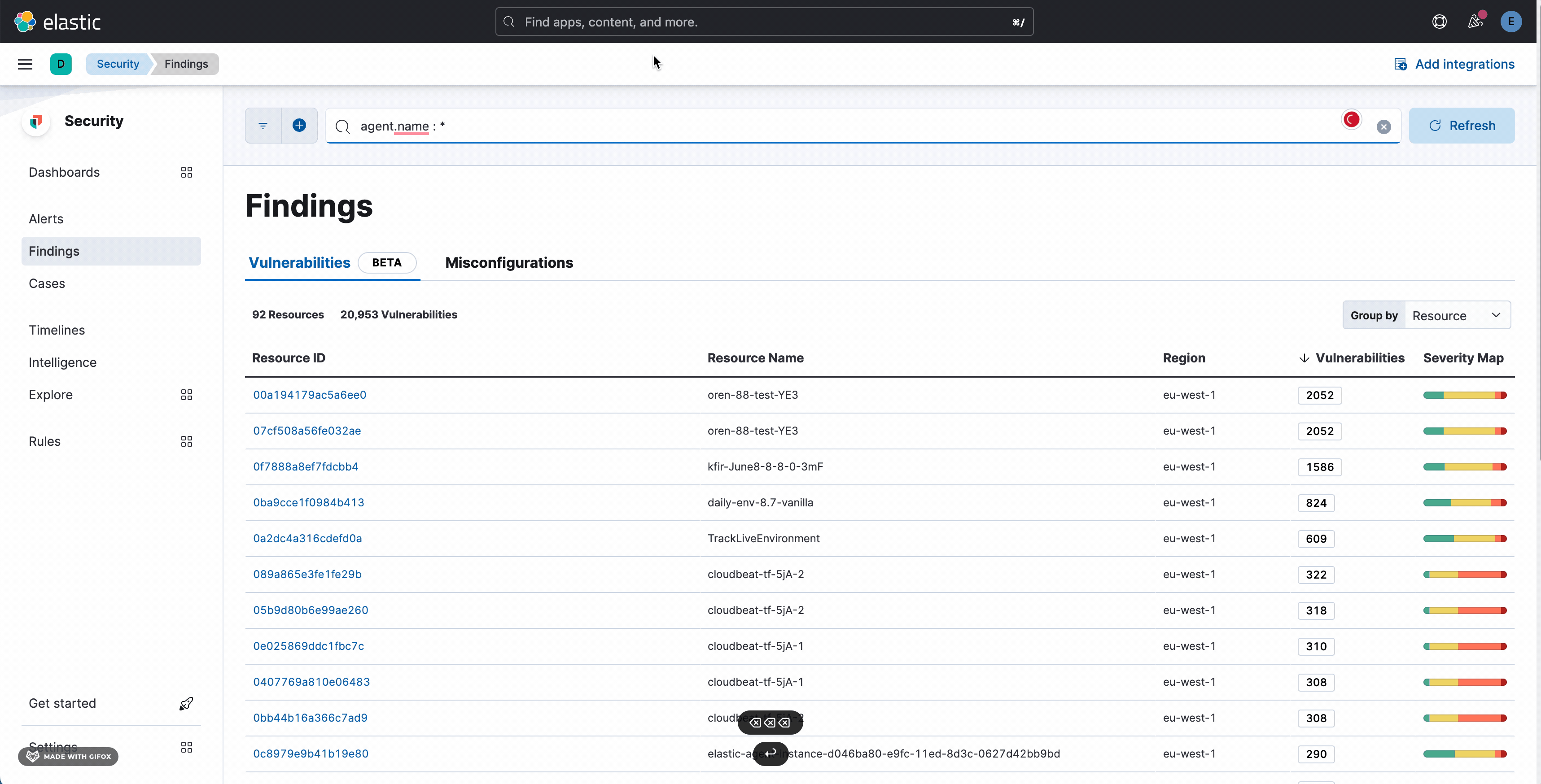 --------- Co-authored-by: Kibana Machine <[email protected]>
|
Thank you @maxcold - I think everything you suggested makes sense. |
|
Just reviewed this ticket. Though I see it's already closed, thanks @maxcold for the thoughtful decisions and excellent work done here. Kudos! 👍 |
|
Evidence: Findings.-.Kibana.-.Google.Chrome.2023-08-22.16-07-31.mp4 |



Kibana version:
BC4
VERSION: 8.8.0
BUILD: 63092
COMMIT: ba9b182
Describe the bug:
Kibana results in an error when searching for a field value with an asterisk (*) and without using double quotes. Even after clearing the search query and refreshing the page, the error continues to appear. The only way to resolve this issue is to log out of Kibana and log back in, which eliminates the error.
Steps to reproduce:
Expected behavior:
Display results matching the search criteria or show empty state with call to action for reset filters if there is no match.
Screen recording (if relevant):
Screen.Recording.2023-05-16.at.1.06.43.PM.mov
The text was updated successfully, but these errors were encountered: